Getting The Risk Management Enterprise To Work
Wiki Article
Getting The Risk Management Enterprise To Work
Table of ContentsThe Greatest Guide To Risk Management EnterpriseGetting The Risk Management Enterprise To WorkRisk Management Enterprise Things To Know Before You Get ThisThe Ultimate Guide To Risk Management EnterpriseAll About Risk Management EnterpriseThe smart Trick of Risk Management Enterprise That Nobody is Talking AboutNot known Details About Risk Management Enterprise
Below are several of its key functions that facilities should understand. So, have a look. Real-Time Risk Assessments and Reduction in this software program enable companies to continually keep track of and assess dangers as they advance. This function leverages real-time information and computerized evaluation to recognize potential risks promptly. When dangers are recognized, the software assists in instant mitigation activities.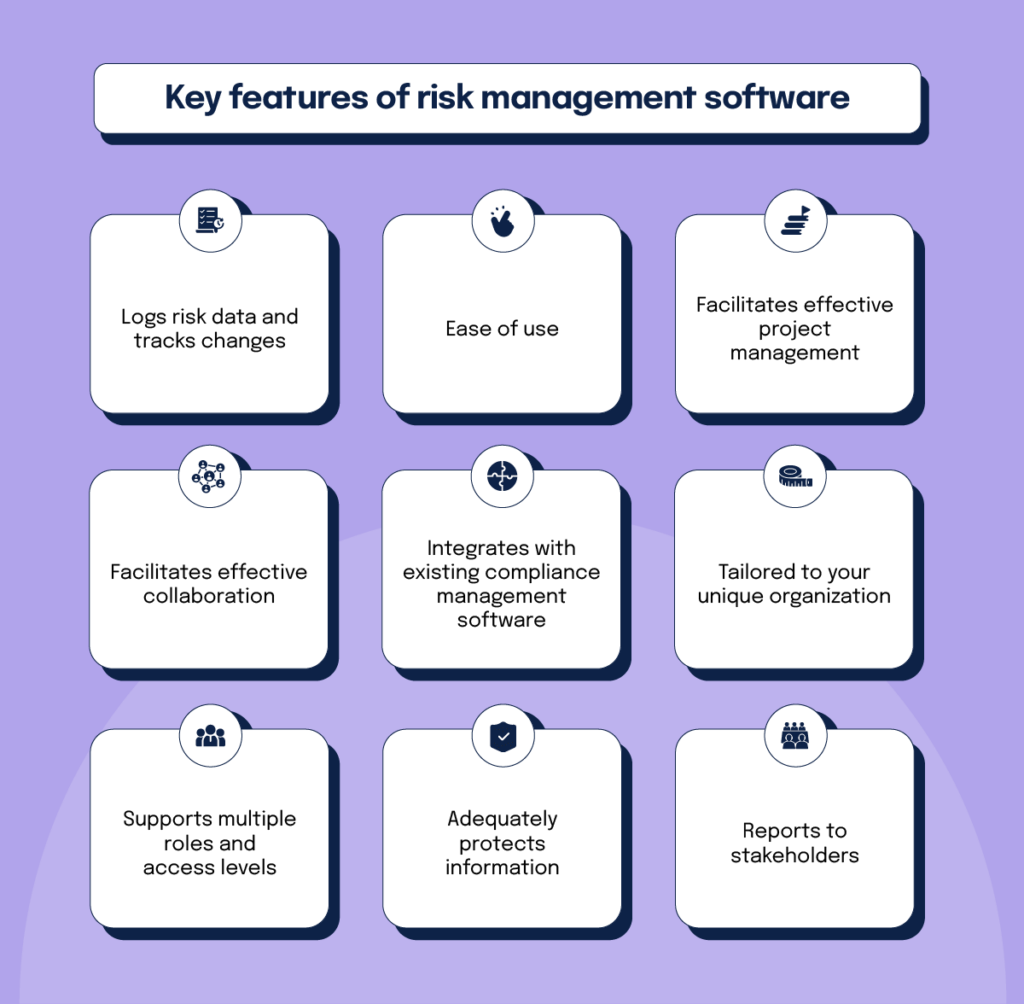
They address the difficulty of recurring risk management by offering devices to monitor dangers constantly. KRIs boost security threat oversight, making sure that potential threats are recognized and taken care of properly.
5 Simple Techniques For Risk Management Enterprise
IT risk management is a subset of business threat monitoring (ERM), made to bring IT take the chance of in line with an organization's threat cravings. IT take the chance of management (ITRM) incorporates the policies, treatments and innovation necessary to lower dangers and susceptabilities, while keeping compliance with suitable regulative needs. Additionally, ITRM seeks to restrict the consequences of destructive occasions, such as protection violations.Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. The ISACA Threat IT framework aligns well with the COBIT 2019 structure, Rose stated.
Business Danger Monitoring Software Application Advancement: Benefits & Qualities, Expense. With technical innovations, dangers are continuously rising. That being said, organizations are a lot more likely to deal with challenges that impact their financial resources, operations, and online reputation. From swiftly varying markets to governing changes and cyber risks, services navigate through a continuously changing sea of dangers.
Risk Management Enterprise Can Be Fun For Anyone
In this blog, we will dive right into the globe of ERM software, discovering what it is, its benefits, features, etc so that you can develop one for your service. Venture Risk Administration (ERM) software is the application program for planning, guiding, arranging, and managing company tasks and improving danger monitoring procedures.With ERM, organizations can make informative decisions to improve the overall strength of the business. Committed ERM systems are important for companies that frequently deal with vast quantities of sensitive information and multiple stakeholders to approve tactical choices.
It can be prevented by making use of the ERM software program system. This system automates regulation compliance management to maintain the company safe and secure and certified.
Risk Management Enterprise - An Overview
You can additionally link existing software systems to the ERM through APIs or by including information manually. Businesses can make use of ERM to assess risks based upon their potential influence for better threat monitoring and mitigation.: Including this function enables individuals to get real-time notifications on their devices concerning any threat that may happen and its effect.
Rather, the software application allows them to establish thresholds for various procedures and send out press notifications in instance of feasible threats.: By integrating data visualization and reporting in the customized ERM software program, organizations can obtain clear understandings about risk trends and performance.: It is required for organizations to adhere to sector compliance and governing criteria.

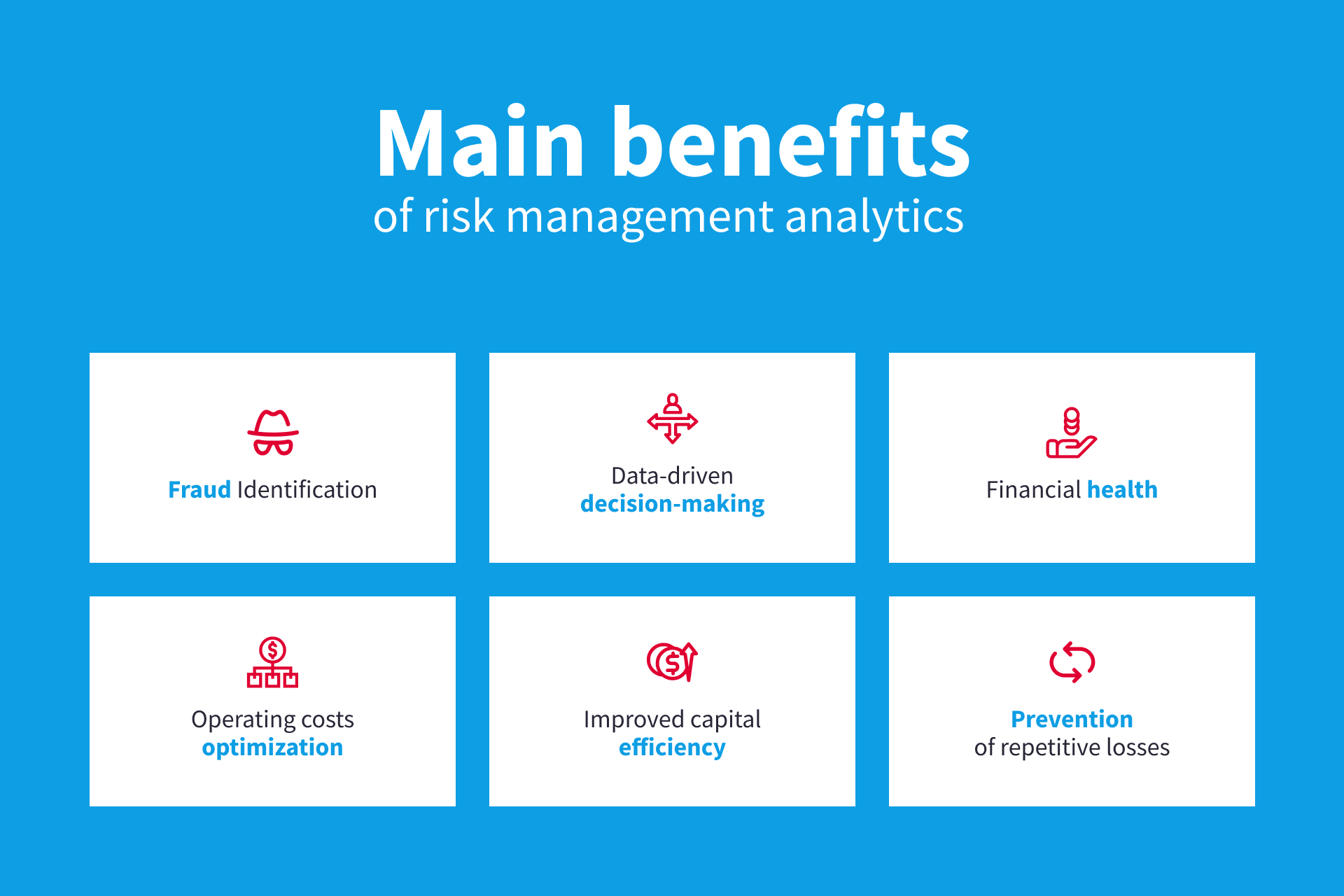
These platforms enable companies to apply best-practice threat management procedures that straighten with sector standards, using a powerful, technology-driven method to determining, examining, and mitigating threats. This blog checks out the advantages of computerized risk administration tools, the areas of danger management they can automate, and the worth they offer a company.
The Single Strategy To Use For Risk Management Enterprise
Groups can establish types with the relevant fields and easily produce different types for various risk kinds. These risk evaluation kinds can be distributed for conclusion using automated operations that send out notifications to the appropriate personnel to finish the types online. If forms are not completed by the due date, after that chaser emails are instantly sent by the system.The control monitoring and control testing process can likewise be automated. Firms can utilize computerized operations to send out normal control test notices and team can go into the outcomes via online forms. Controls can also be monitored by the software by establishing policies to send out notifies based upon control data kept in other systems and spreadsheets that is pulled into the platform by means of API combinations.
Risk management automation software program can additionally support with risk coverage for all degrees of the business. Leaders can view reports on risk direct exposure and control performance via a range of reporting outputs consisting of fixed reports, Power BI interactive records, bowtie analysis, and Monte Carlo simulations. The capacity to draw actual time reports at the touch of a switch reduces out arduous data adjustment tasks leaving risk teams with more time to evaluate the information and advise business on the very best training course of action.
Organizations operating in competitive, fast-changing markets can't afford delays or inefficiencies in dealing with possible dangers. Typical danger monitoring making use of hands-on spreadsheet-based processes, while acquainted, commonly lead to fragmented data, time-consuming coverage, and an increased likelihood of human error.
Everything about Risk Management Enterprise
This makes certain threat registers are always existing and lined up with business goals. Conformity is one more important vehicle driver for automating risk management. Standards like ISO 31000, CPS 230 and COSO all offer assistance around danger management best practices and control frameworks, and automated threat management tools are structured to straighten with these requirements assisting firms to fulfill most commonly used danger administration requirements.Seek danger software program systems with an authorizations pecking order to conveniently establish operations for threat rise. This performance enables you to customize the view for each user, so they only see the data relevant to them. Make certain the ERM software uses individual tracking so you can see who entered what information and when.
Seek out devices that offer job danger management capabilities to handle your tasks and portfolios and the associated threats. The advantages of adopting danger monitoring automation software prolong far past efficiency.
Risk Management Enterprise for Beginners
While the instance for automation is engaging, executing a threat management platform is not without its challenges. For one, data quality is important. Automated systems rely upon exact, up-to-date info to deliver significant insights. To overcome the challenges of risk monitoring automation, organizations must purchase data cleaning and governance to make sure a solid foundation for executing an automated platform.Automation in threat administration encourages services to transform their strategy to risk and build a more powerful foundation for the future (Risk Management Enterprise). The inquiry is no more whether to automate danger monitoring, it's just how quickly you can begin. To see the Riskonnect in activity,
The response usually lies in just how well threats are anticipated and taken care of. Project administration software serves as the navigator in the tumultuous waters of task implementation, offering tools that identify and examine threats and develop approaches to reduce them effectively.
Report this wiki page